Innovation, Agility and Securing the Mobile World in 2021
Lohrman on Security
FEBRUARY 21, 2021

Tech Republic Security
FEBRUARY 22, 2021
A study on CIO and CISO prioritization showed these two areas are most important this year. Cloud security is another area high on their lists.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
FEBRUARY 22, 2021
An ever-evolving and rampant form of cybercrime that targets emails as the potential medium to conduct fraud is known as Business Email Compromise. Targeting commercial, government as well as non-profit organizations, BEC can lead to huge amounts of data loss, security breach, and compromised financial assets.

CSO Magazine
FEBRUARY 23, 2021
Cybersecurity audit fatigue has become a very real issue for organizations that are required to comply with multiple government, industry, and internal requirements.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Krebs on Security
FEBRUARY 23, 2021
Easily the most sophisticated skimming devices made for hacking terminals at retail self-checkout lanes are a new breed of PIN pad overlay combined with a flexible, paper-thin device that fits inside the terminal’s chip reader slot. What enables these skimmers to be so slim? They draw their power from the low-voltage current that gets triggered when a chip-based card is inserted.

Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.” From a blog post : The report suggests a comprehensive framework for understanding and assessing the risks posed by Chinese technology platforms in the United States and developing tailored responses. It starts from the common view of the signatories — one reflected in numerous publicly available threat assessments — that China’s power is
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
FEBRUARY 24, 2021
BlackBerry researchers see more double-extortion ransomware attacks, attackers demanding ransom from healthcare patients, and rising bitcoin prices driving the growth of ransomware.

Krebs on Security
FEBRUARY 25, 2021
The U.S. Labor Department’s inspector general said this week that roughly $100 million in fraudulent unemployment insurance claims were paid in 2020 to criminals who are already in jail. That’s a tiny share of the estimated tens of billions of dollars in jobless benefits states have given to identity thieves in the past year. To help reverse that trend, many states are now turning to a little-known private company called ID.me.

Schneier on Security
FEBRUARY 23, 2021
Alex Birsan writes about being able to install malware into proprietary corporate software by naming the code files to be identical to internal corporate code files. From a ZDNet article : Today, developers at small or large companies use package managers to download and import libraries that are then assembled together using build tools to create a final app.

The Last Watchdog
FEBRUARY 23, 2021
Human suffering and economic losses weren’t the only two things that escalated with the spread of Covid 19 last year. Related: Can ‘SASE’ help companies secure connectivity? Network breaches also increased steadily and dramatically month-to-month in 2020. This development is delineated in a recent report from technology research firm Forrester.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
FEBRUARY 23, 2021
DDoS, SQL injection and man-in-the-middle are just a few of the attacks that can compromise your network. Tom Merritt lists five things to know about network attacks.

Zero Day
FEBRUARY 26, 2021
There's been a 2,000% increase of new malware written in Go over the past few years.

Schneier on Security
FEBRUARY 24, 2021
Researchers found, and Microsoft has patched, a vulnerability in Windows Defender that has been around for twelve years. There is no evidence that anyone has used the vulnerability during that time. The flaw, discovered by researchers at the security firm SentinelOne, showed up in a driver that Windows Defender — renamed Microsoft Defender last year — uses to delete the invasive files and infrastructure that malware can create.

Security Affairs
FEBRUARY 26, 2021
French experts spotted a new Ryuk ransomware variant that implements self-spreading capabilities to infect other devices on victims’ local networks. Experts from French national cyber-security agency ANSSI have spotted a new Ryuk ransomware variant that implements worm-like capabilities that allow within local networks. “On top of its usual functions, this version holds a new attribute allowing it to self replicate over the local network.” reads the report published by the ANSS

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
FEBRUARY 23, 2021
With the shift to remote learning, schools are facing greater security risks and smaller financial margins, says BlueVoyant.
The Hacker News
FEBRUARY 25, 2021
Cybersecurity researchers today unwrapped a new campaign aimed at spying on vulnerable Tibetan communities globally by deploying a malicious Firefox extension on target systems.

Schneier on Security
FEBRUARY 22, 2021
Really good op-ed in the New York Times about how vulnerable the GPS system is to interference, spoofing, and jamming — and potential alternatives. The 2018 National Defense Authorization Act included funding for the Departments of Defense, Homeland Security and Transportation to jointly conduct demonstrations of various alternatives to GPS, which were concluded last March.
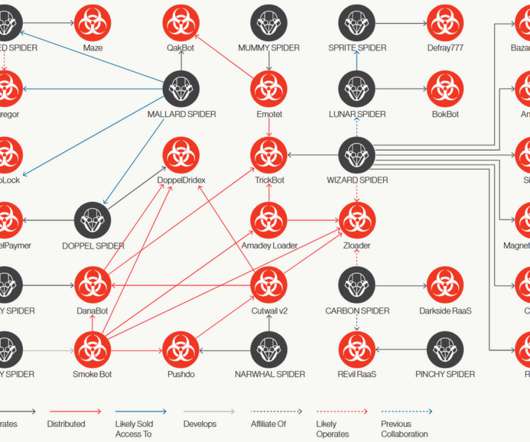
Zero Day
FEBRUARY 25, 2021
CrowdStrike puts together a list of connections and how cybercrime groups cooperate with each other.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Tech Republic Security
FEBRUARY 22, 2021
Most organizations don't give the same thought and attention to their non-human workers, such as bots, RPAs and service accounts, as they do human workers and identity lifecycles.

SecureList
FEBRUARY 25, 2021
Lazarus targets defense industry with ThreatNeedle (PDF). We named Lazarus the most active group of 2020. We’ve observed numerous activities by this notorious APT group targeting various industries. The group has changed target depending on the primary objective. Google TAG has recently published a post about a campaign by Lazarus targeting security researchers.

Schneier on Security
FEBRUARY 26, 2021
Excellent Brookings paper: “ Why data ownership is the wrong approach to protecting privacy.” From the introduction: Treating data like it is property fails to recognize either the value that varieties of personal information serve or the abiding interest that individuals have in their personal information even if they choose to “sell” it.

Zero Day
FEBRUARY 24, 2021
Ukrainian officials blame "one of the hacker spy groups from the Russian Federation.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Tech Republic Security
FEBRUARY 25, 2021
The Stanford Internet Observatory alleged that the Chinese government may have had access to audio data from Clubhouse. Here's what users should know.
The Hacker News
FEBRUARY 24, 2021
The cybersecurity world is constantly evolving to new forms of threats and vulnerabilities. But ransomware proves to be a different animal—most destructive, persistent, notoriously challenging to prevent, and is showing no signs of slowing down.

Graham Cluley
FEBRUARY 26, 2021
UK energy firm Npower has scrapped its smartphone app following an attack by hackers that saw some users' accounts accessed and personal information stolen.

Zero Day
FEBRUARY 23, 2021
Bombardier is the latest in a long string of hacks caused by companies using old versions of the Accellion FTA file-sharing server.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
FEBRUARY 26, 2021
The benefits of working remotely are numerous, but there are significant hidden costs that need to be factored in.

WIRED Threat Level
FEBRUARY 22, 2021
The hackers used the agency’s EpMe exploit to attack Windows devices years before the Shadow Brokers leaked the agency’s zero-day arsenal online.

Security Affairs
FEBRUARY 20, 2021
Sequoia Capital, one of the most prominent venture capital firms, told its investors that an unauthorized third party had access to their information. Sequoia Capital, one of the most prominent venture capital firms that focus on the technology industry, discloses a data breach. The company informed its investors that an unauthorized third party had access to their personal and financial information.

Zero Day
FEBRUARY 24, 2021
IBM says attack rates have doubled against medical entities since the pandemic began.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content