Iran-linked MERCURY APT behind destructive attacks on hybrid environments
Security Affairs
APRIL 10, 2023
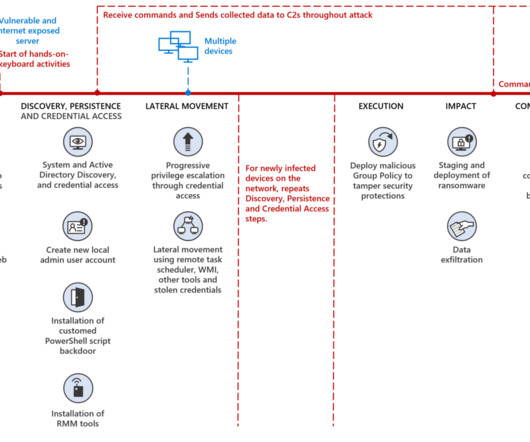
Both groups used MULLVAD VPN. The attackers were able to interfere with security tools using Group Policy Objects (GPO). Once bypassed the security defenses, the attackers deployed the ransomware payload in the NETLOGON shares on several domain controllers. DEV-1084 used Rport and a customized version of Ligolo.
















Let's personalize your content