Exposed security cameras in Israel and Palestine pose significant risks
Security Affairs
OCTOBER 10, 2023
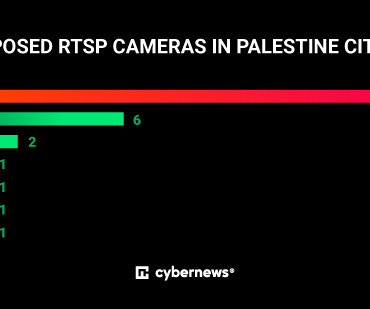
Many poorly configured security cameras are exposed to hacktivists in Israel and Palestine, placing the owners using them and the people around them at substantial risk. While this communication system is useful for transferring real-time data, it offers neither encryption nor lockout mechanisms against password-guessing.














Let's personalize your content