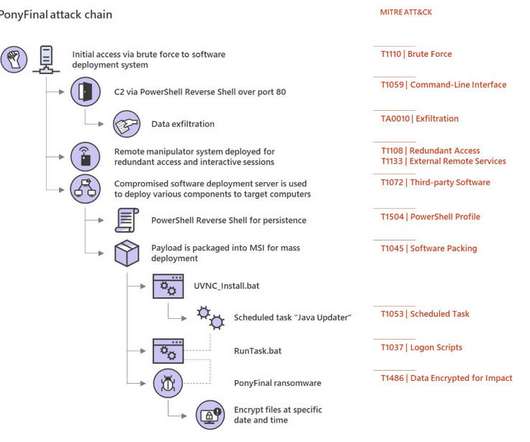
Microsoft warns about ongoing PonyFinal ransomware attacks
Security Affairs
MAY 27, 2020
pic.twitter.com/Q3BMs7fSvx — Microsoft Security Intelligence (@MsftSecIntel) May 27, 2020. Learn how to build organizational security hygiene to prevent human-operated attacks: [link] — Microsoft Security Intelligence (@MsftSecIntel) May 27, 2020. The ransom note contains the payment instructions.














Let's personalize your content