Targeted assets: The need for cyber resilient infrastructure
Webroot
MAY 12, 2021
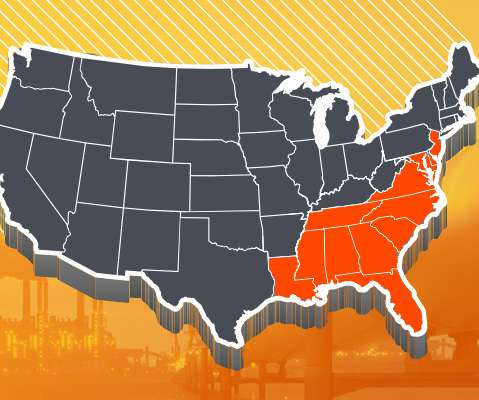
As of now, we still don’t know much about the ransomware attack against the operators of the Colonial Pipeline. The FBI has confirmed that Darkside, a ransomware as a service (RaaS) group, was behind the attack but background on that group is about the only place where information is plentiful. . infrastructure cybersecurity?






















Let's personalize your content