Cisco Secure Endpoint Shines in the 2022 MITRE® Engenuity ATT&CK Evaluation
Cisco Security
APRIL 19, 2022
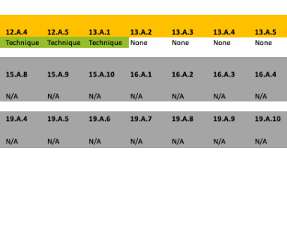
Overall, Cisco Secure Endpoint proved it can stop Wizard Spider and Sandworm attack campaigns early in the kill chains and provided analytic detections at the MITRE ATT&CK technique level across each step of its respective kill chains. Blocked 5 of 6 Tests. This round focused on threat actors Wizard Spider and Sandworm.













Let's personalize your content