Simplify Network Security with Cisco Secure Firewall-as-a-service (FWaaS) on AWS
Cisco Security
NOVEMBER 29, 2021
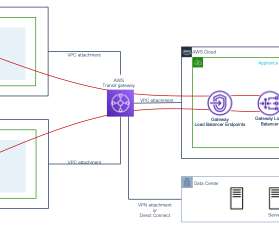
With traditional firewalls, network security teams are charged with the heavy lifting of deploying new solutions. According to Gartner, by 2025, 30% of new deployments of distributed branch-office firewalls will switch to firewall-as-a-service, up from less than 10% in 2021. Introduction. Starting with version 7.1

































Let's personalize your content