3.5m IP cameras exposed, with US in the lead
Security Affairs
DECEMBER 14, 2022
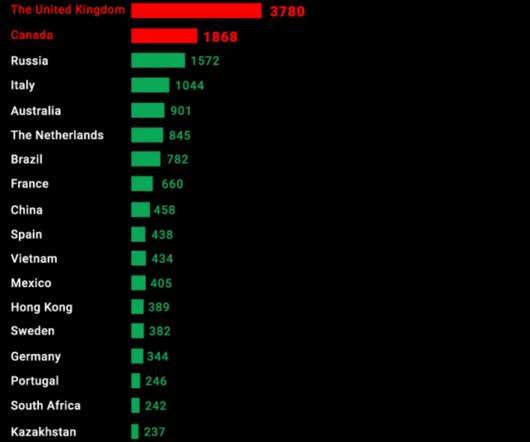
The number of internet-facing cameras in the world is growing exponentially. Businesses and homeowners increasingly rely on internet protocol (IP) cameras for surveillance. New research by Cybernews shows an exponential rise in the uptake of internet-facing cameras. Surge in internet-facing cameras.













Let's personalize your content