China-linked APT BlackTech was spotted hiding in Cisco router firmware
Security Affairs
SEPTEMBER 27, 2023
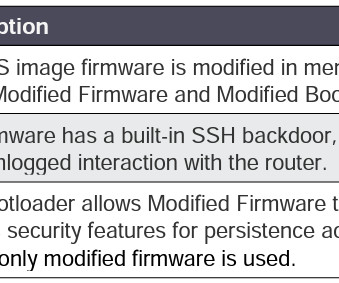
US and Japanese authorities warn that a China-linked APT BlackTech planted backdoor in Cisco router firmware to hack the businesses in both countries. The group targeted organizations in multiple sectors, including defense, government, electronics, telecommunication, technology, media, telecommunication industries.

















Let's personalize your content