Ghost Ransomware a Persistent Global Threat to Critical Infrastructure
SecureWorld News
FEBRUARY 20, 2025
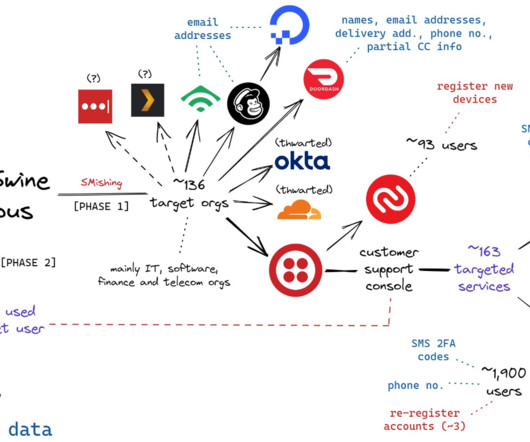
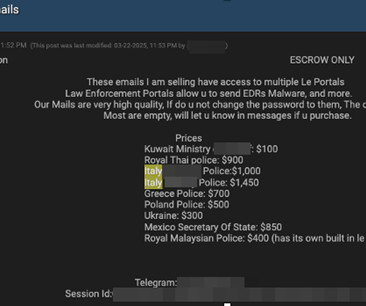
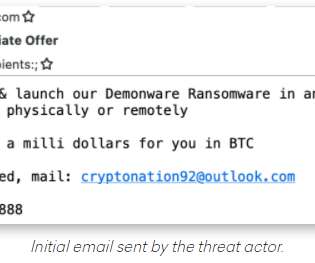
The FBI, CISA, and MS-ISAC have issued a joint cybersecurity advisory warning organizations about Ghost (Cring) ransomware, a sophisticated cyber threat that has been compromising critical infrastructure, businesses, and government entities worldwide. All they need is one successful attempt to gain initial access."
















































Let's personalize your content