Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade detection
Security Affairs
NOVEMBER 18, 2020
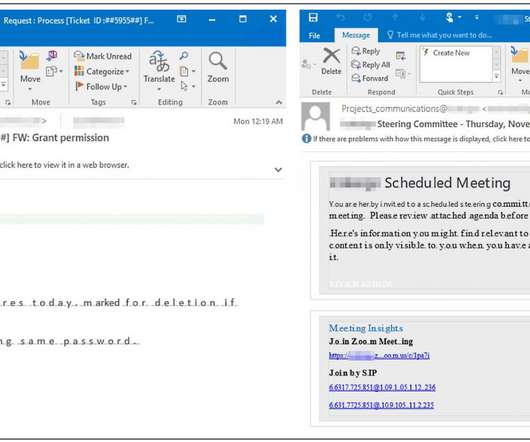
. “We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message published by Microsoft via Twitter. pic.twitter.com/YpUVEfmlUH — Microsoft Security Intelligence (@MsftSecIntel) November 16, 2020.














Let's personalize your content