News alert: INE Security spotlights healthcare companies facing rising exposure to costly breaches
The Last Watchdog
MARCH 24, 2025
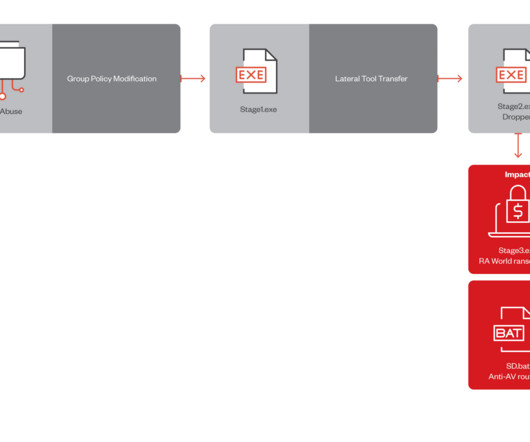
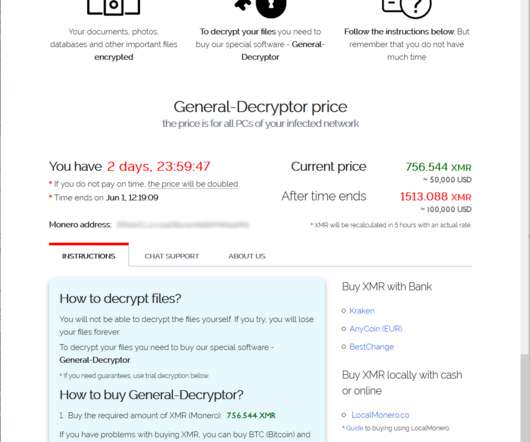
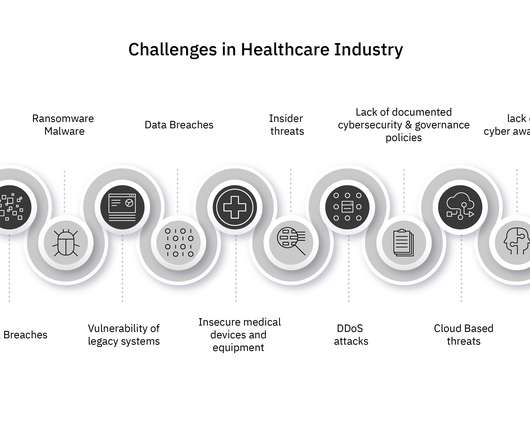
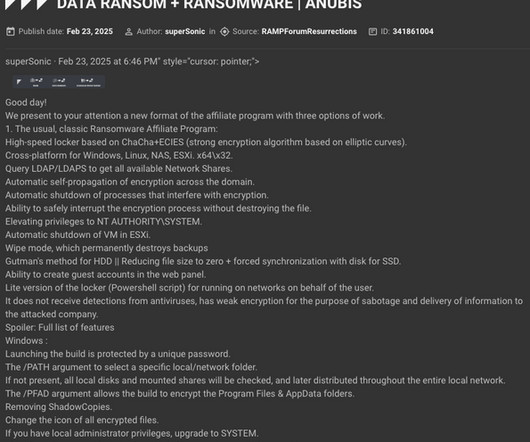
24, 2025, CyberNewswire – – INE Security , a global provider of cybersecurity training and certification, today announced its initiative to spotlight the increasing cyber threats targeting healthcare institutions. Recent reports show healthcare has endured a record wave of cyber breaches. Cary, NC, Mar.














































Let's personalize your content