Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
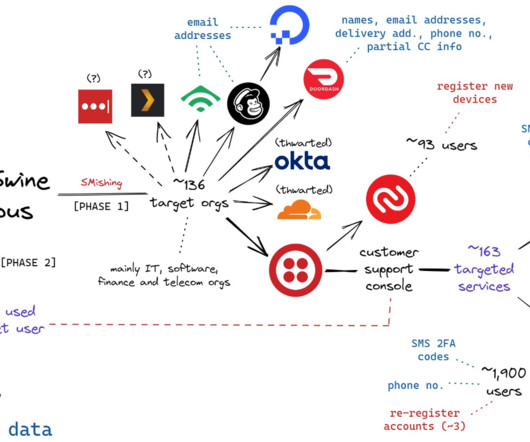
The feds then obtained records from Virgin Media, which showed the address was leased for several months to Tyler Buchanan , a 22-year-old from Dundee, Scotland. The Spanish police told local media that Buchanan, who allegedly went by the alias “ Tylerb ,” at one time possessed Bitcoins worth $27 million. .”














































Let's personalize your content