Retail Cybersecurity: The Importance of Compliance and Risk Management
Security Boulevard
FEBRUARY 27, 2024
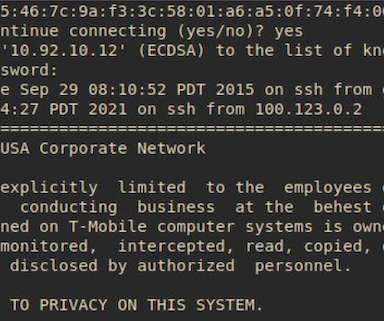
However, these gaps in security are now becoming a critical issue, especially in light of evolving compliance standards like the Payment Card Industry Data Security Standard (PCI DSS), which releases version 4.0 These numbers highlight the importance of robust and proactive security strategies. What's at Stake? million U.S.,



























Let's personalize your content