Fake Etsy invoice scam tricks sellers into sharing credit card information
Malwarebytes
FEBRUARY 12, 2025
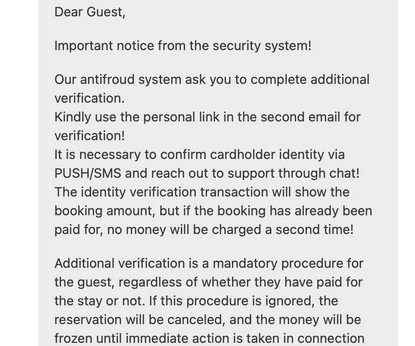
The site may ask for more information than Etsy would normally request for verification – like your full name, address, and even your credit card details. In the final step, the counterfeit page will prompt you to enter your credit card details , supposedly to confirm your billing information or validate your seller account.















































Let's personalize your content