HTML Smuggling technique used in phishing and malspam campaigns
Security Affairs
NOVEMBER 12, 2021
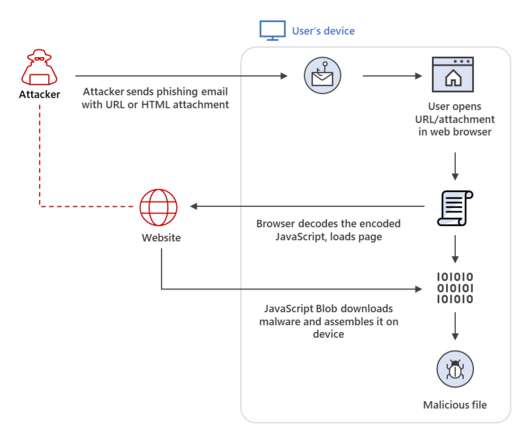
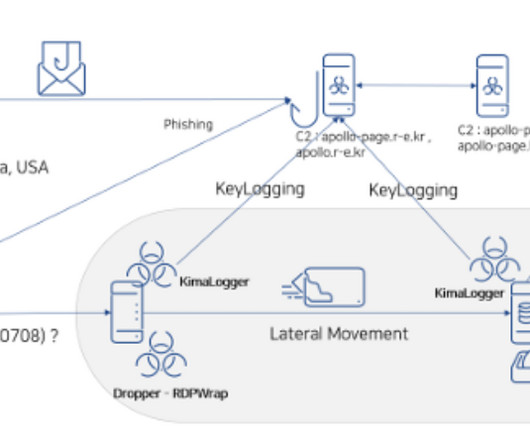
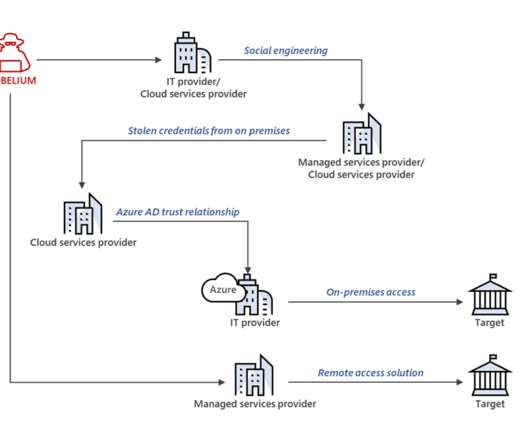
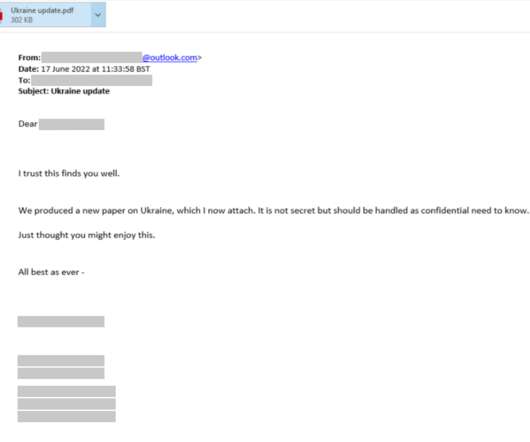
Threat actors are increasingly using the HTML smuggling technique in phishing campaigns, Microsoft researchers warn. Microsoft experts warn that threat actors are increasingly using the HTML smuggling technique in phishing campaigns to stealthily deliver threats. — Microsoft Security Intelligence (@MsftSecIntel) July 23, 2021.


















Let's personalize your content