Hacking IoT Security with Aaron Guzman
Security Boulevard
AUGUST 30, 2021
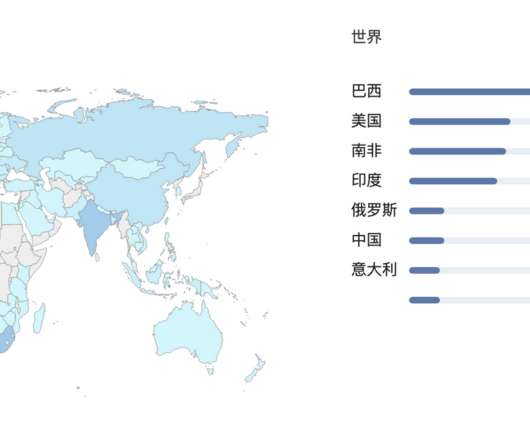
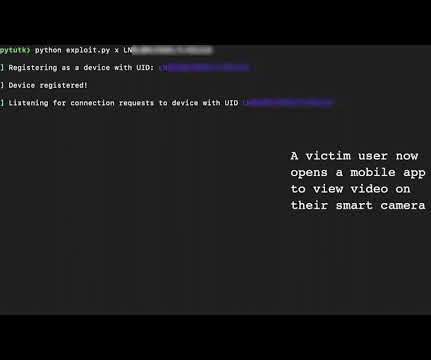
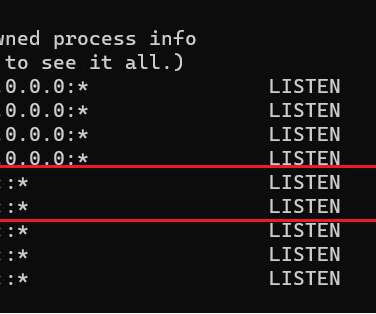
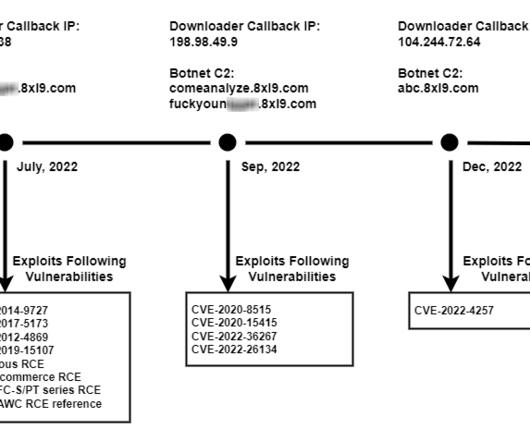
Sources and Sinks interviews car hacker and IoT security expert, Aaron Guzman. Information security is no longer staying on our laptops and in our browsers. As our devices become increasingly interconnected too, we have to start thinking about the security of our IoT devices.







































Let's personalize your content