GUEST ESSAY: Sure steps to achieve a robust employee cybersecurity awareness training regimen
The Last Watchdog
OCTOBER 24, 2022
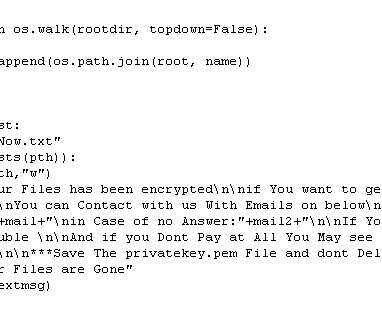
Employee security awareness is the most important defense against data breaches. Related: Leveraging security standards to protect your company. It involves regularly changing passwords and inventorying sensitive data. Create security awareness for employees.

























Let's personalize your content