STEPS FORWARD: Regulators are on the move to set much needed IoT security rules of the road
The Last Watchdog
SEPTEMBER 5, 2023
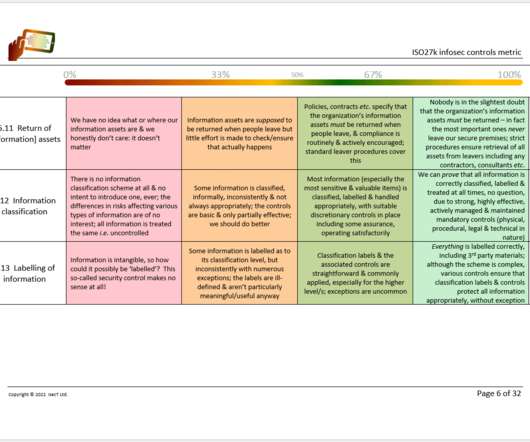
New government rules coupled with industry standards meant to give formal shape to the Internet of Things (IoT) are rapidly quickening around the globe. Related: The need for supply chain security This is to be expected. After all, government mandates combined with industry standards are the twin towers of public safety.



















Let's personalize your content