Akira ransomware gang used an unsecured webcam to bypass EDR
Security Affairs
MARCH 8, 2025
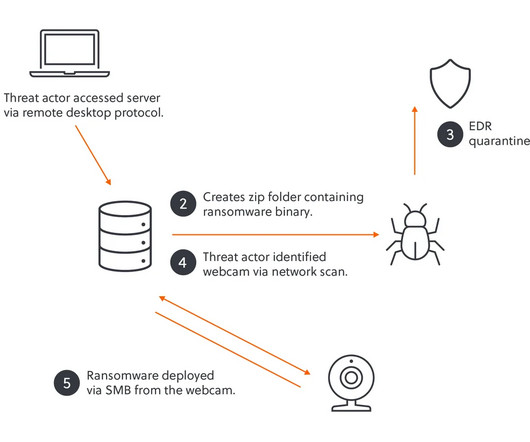
The Akira ransomware gang exploited an unsecured webcam to bypass EDR and launch encryption attacks on a victim’s network. Cybersecurity researchers at S-RM team discovered a novel attack technique used by the Akira ransomware gang. Realizing EDR was active, they pivoted by scanning the network for vulnerable devices.




























Let's personalize your content