Crazy Evil gang runs over 10 highly specialized social media scams
Security Affairs
FEBRUARY 3, 2025
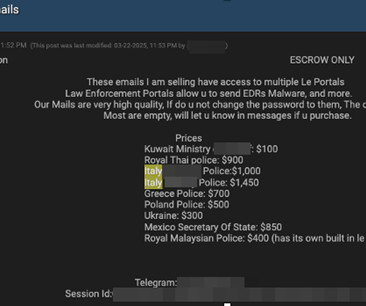
The Russian-speaking Crazy Evil group runs over 10 social media scams, tricking victims into installing StealC, AMOS, and Angel Drainer malware. ” Crazy Evil is referred as a traffer team, which is a group of social engineering specialists tasked with redirecting legitimate traffic to malicious landing pages.


















































Let's personalize your content