Hackers Use Malicious PDFs, pose as USPS in Mobile Phishing Scam
Security Boulevard
JANUARY 27, 2025
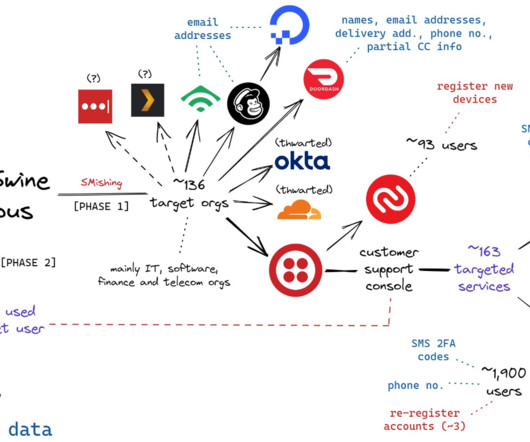
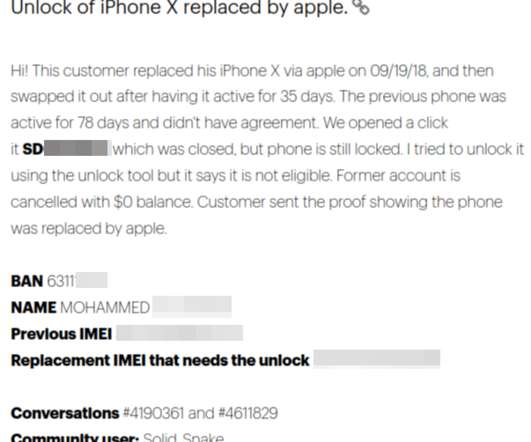
A large-scale phishing campaign is using PDF files and hidden malicious links, as well as posing at the U.S. Postal Service, in phishing campaign targeting mobile device users in hope that victims will divulge credentials and personal information, Zimperium researchers say.

















































Let's personalize your content