How to build a zero trust ecosystem
SC Magazine
MAY 19, 2021
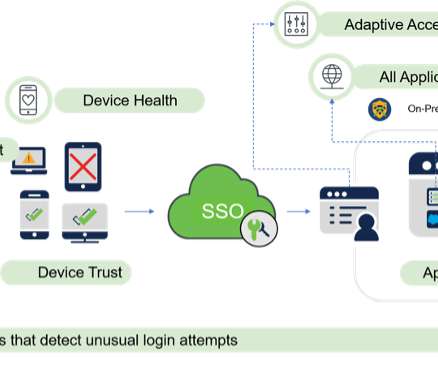
With its tailored controls, micro-perimeters and trust-nothing approach to access, Zero Trust gives CISOs confidence that their security program can secure their remote workforce and meet regulatory compliance requirements. Examples of identity types are the user, device, applications, data, network traffic and behaviors.































Let's personalize your content