Browser Isolation: The Missing Piece in Your Security Puzzle
SecureWorld News
APRIL 9, 2023
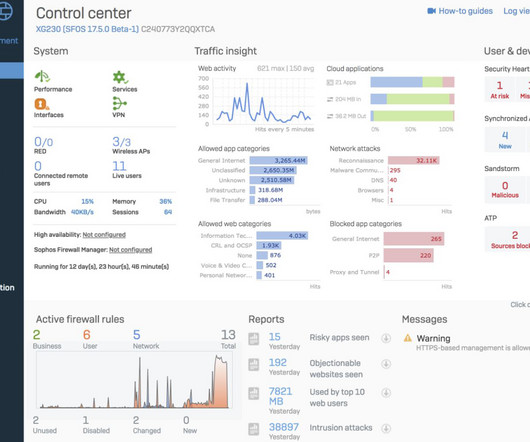
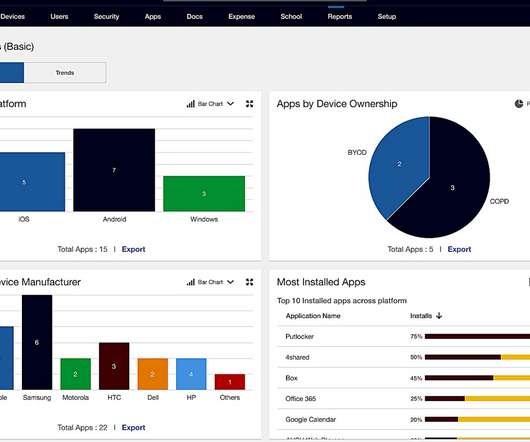
In contrast to typical methods of defending against web attacks, browser isolation utilizes a Zero Trust strategy that does not rely on filtering based on threat models or signatures. Corporate employees frequently utilize the vast resources of the internet to address various business issues on a daily basis.


























Let's personalize your content