Mapping CVEs and ATT&CK Framework TTPs: An Empirical Approach
NopSec
OCTOBER 11, 2022
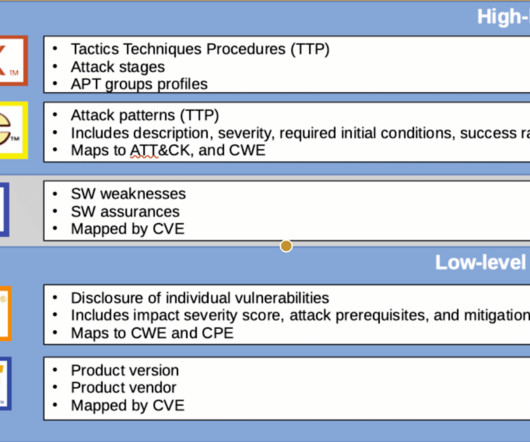
The CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability, mostly from the technical standpoint. (or Download the free playbook today. FAQ Question #1: What is the CVE Program?















Let's personalize your content