How to improve security awareness and training for your employees
Tech Republic Security
OCTOBER 27, 2022
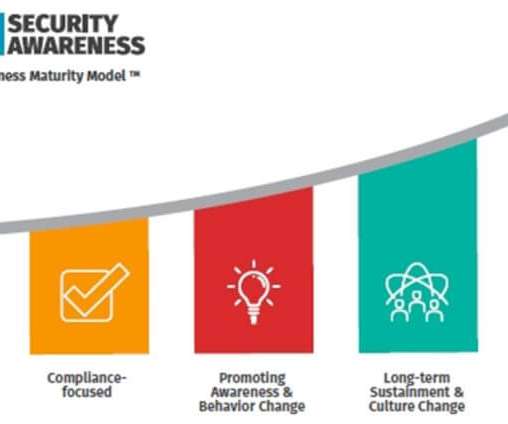
Just training people periodically using generic content won’t help them or your organization reduce the risk of security threats, says Egress. The post How to improve security awareness and training for your employees appeared first on TechRepublic.























Let's personalize your content