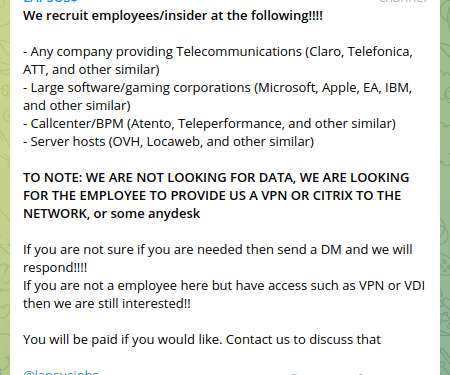
Lapsus$ Ransomware Group is hiring, it announced recruitment of insiders
Security Affairs
MARCH 11, 2022
Lapsus$ Ransomware gang is looking for insiders willing to sell remote access to major technology corporations and ISPs. Thursday, March 10, Lapsus$ ransomware gang announced they’re starting to recruit insiders employed within major technology giants and ISPs, such companies include Microsoft, Apple, EA Games and IBM.




















Let's personalize your content