New ZLoader malware campaign hit more than 2000 victims across 111 countries
Security Affairs
JANUARY 10, 2022
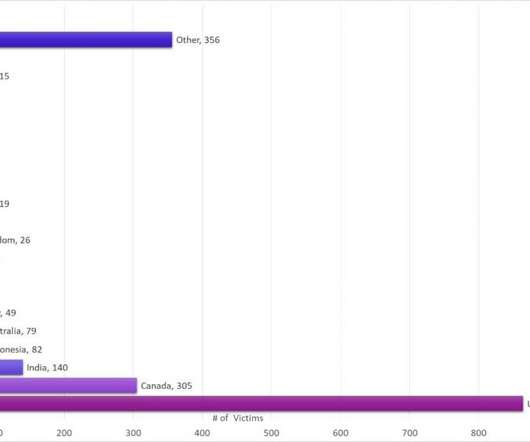
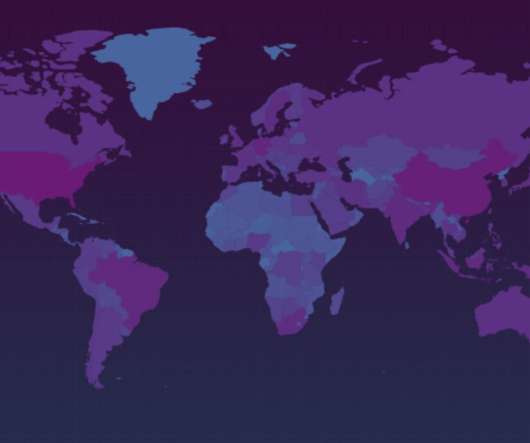
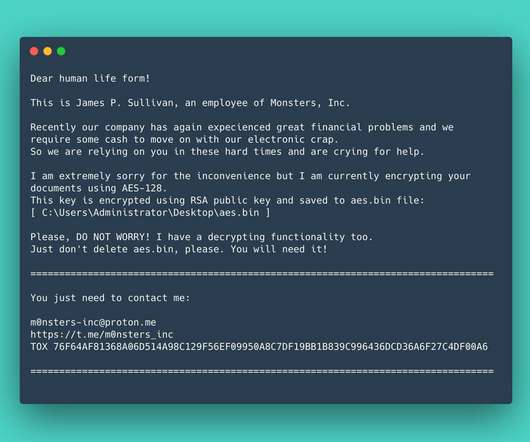
The malware campaign is still active and threat actors have already stolen data and credentials of more than 2000 victims across 111 countries as of 2 Jan 2022. Experts attribute this campaign to MalSmoke cybercrime group due to similarities with past attacks. banking Trojan and was used to spread Zeus-like banking trojan (i.e.







































Let's personalize your content