Approximately 2000 Citrix NetScaler servers were backdoored in a massive campaign
Security Affairs
AUGUST 16, 2023
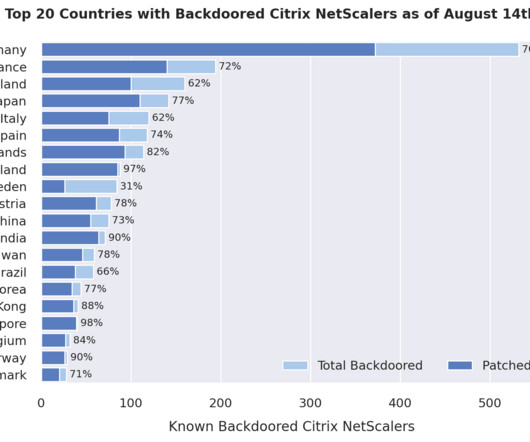
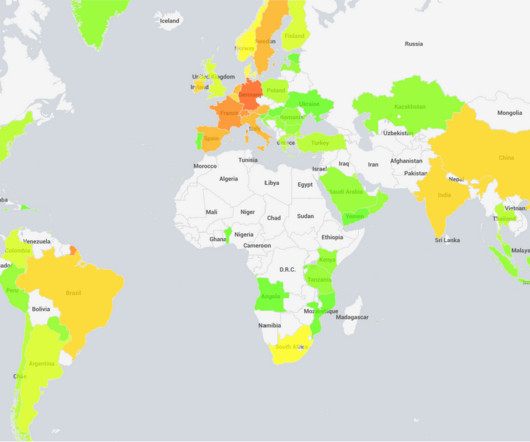
System administrators need to be aware that adversaries can exploit edge devices to place backdoors that persist even after updates and / or reboots.” As of August 14, most of the backdoored instances are in Germany, France and Switzerland. ” concludes the report.”As












Let's personalize your content