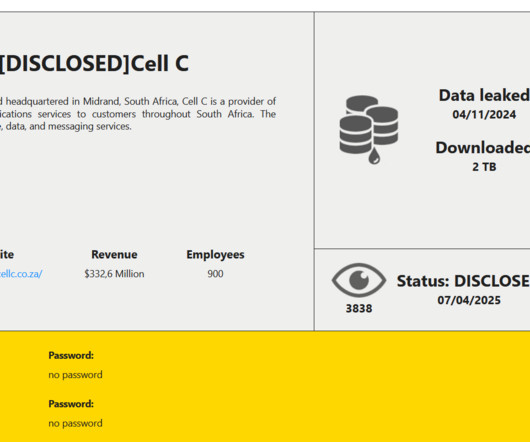
South African telecom provider Cell C disclosed a data breach following a cyberattack
Security Affairs
APRIL 13, 2025
The company founded in 2001 offers prepaid and postpaid mobile plans, data bundles and internet services, fiber broadband, roaming and international calling, SIM-only plans and device deals. Unlike other extortion group, the gang doesnt encrypt data, but focuses on data theft to speed up its activity. Victims include AMD and Keralty.












Let's personalize your content