Anton’s Alert Fatigue: The Study
Anton on Security
NOVEMBER 6, 2024
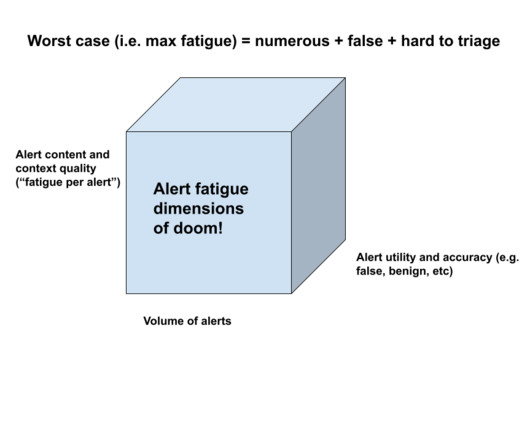
In theory they should have decreased over the last 25 years, if we believe that security technology is improving. We tried many, many types of so-called risk prioritization of alerts. I cringe a bit since I feel that I am dispensing 2001-style advice here (“tune your NIDS!”) I frankly don’t know and don’t have a gut feel here.


































Let's personalize your content