Anton’s Alert Fatigue: The Study
Anton on Security
NOVEMBER 6, 2024
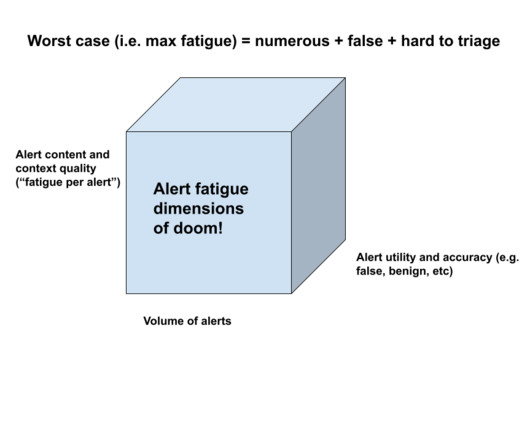
Frankly, I don’t recall any year during which this problem was considered close to being solved, pay no heed to shrill vendor marketing. At the time, these were alerts from firewalls and IDS systems. IP became system name, became asset role/owner, past history was added and a lot of other things (hi 2006 SIEM Vendor A).


















Let's personalize your content