Researchers Decrypted Qakbot Banking Trojan’s Encrypted Registry Keys
The Hacker News
JANUARY 13, 2022
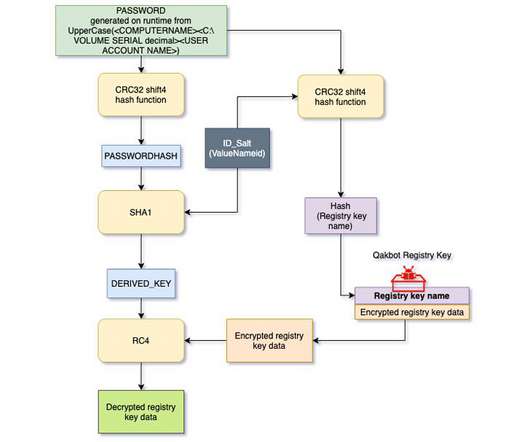
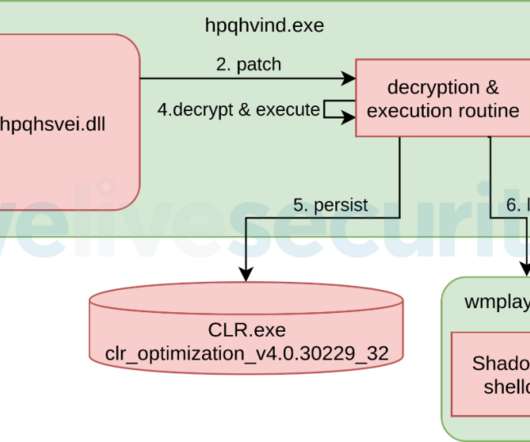
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry. Qakbot, also known as QBot, QuackBot and Pinkslipbot, has been observed in the wild since 2007.





































Let's personalize your content