Bitdefender offers mobile security to chats on messaging apps
CyberSecurity Insiders
NOVEMBER 8, 2022
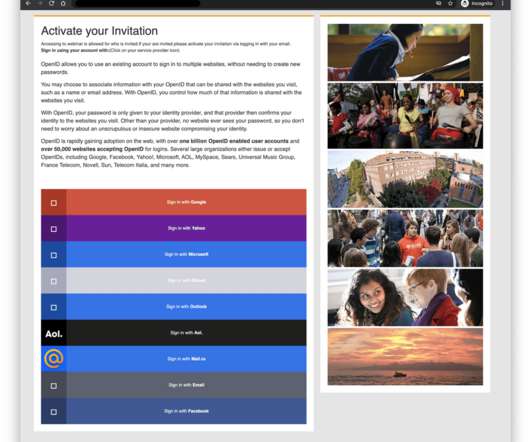
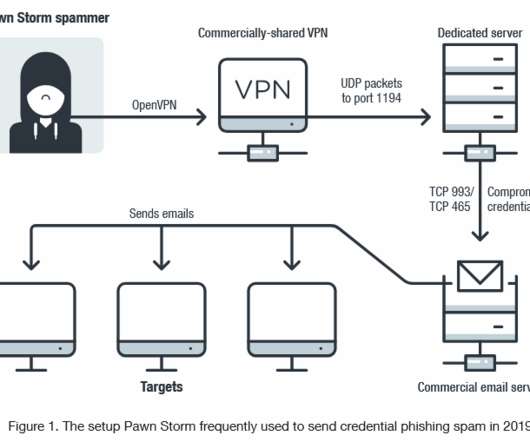
BitDefender Mobile Security feature assists customers in protecting against malware spread and phishing scams. However, the feature is available for a premium of $16 per year and includes a VPN access in the pay. It covers devices operating on Windows, macOS, Android and iOS devices, which is outstanding.












Let's personalize your content