China-linked APT BlackTech was spotted hiding in Cisco router firmware
Security Affairs
SEPTEMBER 27, 2023
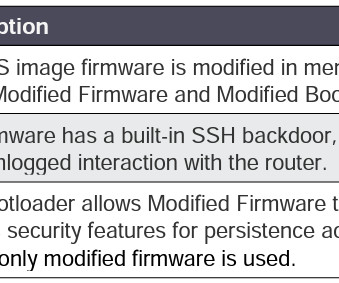
US and Japanese authorities warn that a China-linked APT BlackTech planted backdoor in Cisco router firmware to hack the businesses in both countries. BlackTech is a Chinese APT group that has been active since at least 2010 and that known for conducting cyber espionage campaigns in Asia aimed at entities in Hong Kong, Japan, and Taiwan.


















Let's personalize your content