Both Mirai and Hoaxcalls IoT botnets target Symantec Web Gateways
Security Affairs
MAY 19, 2020
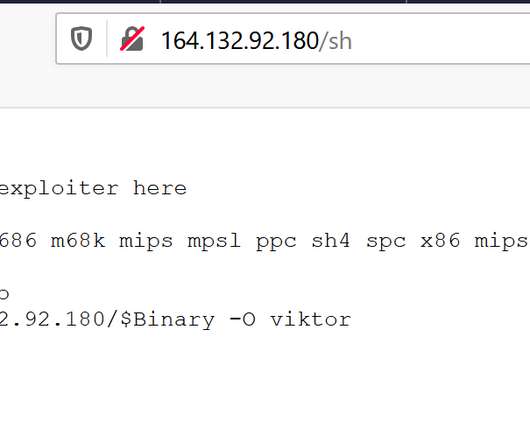
Palo Alto Networks Unit 42 researchers observed both the Mirai and Hoaxcalls botnets using an exploit for a post-authentication Remote Code Execution vulnerability in legacy Symantec Web Gateways 5.0.2.8. Experts note that the exploit is only effective for authenticated sessions and the affected devices are End of Life (EOL) from 2012.
















Let's personalize your content