New UEFI bootkit used to backdoor Windows devices since 2012
Bleeping Computer
OCTOBER 5, 2021
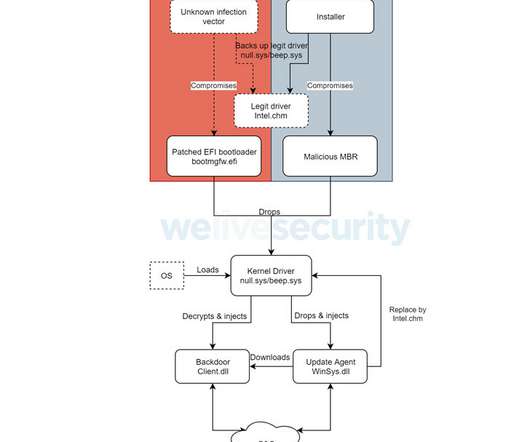
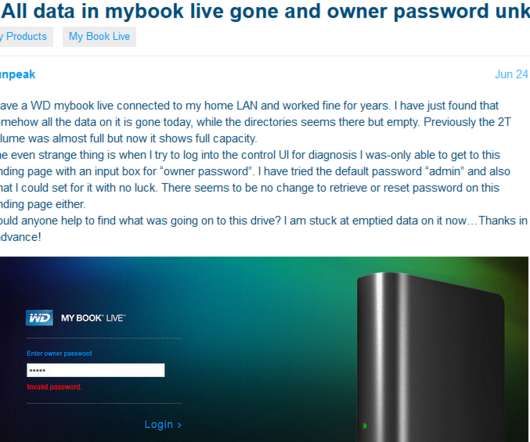
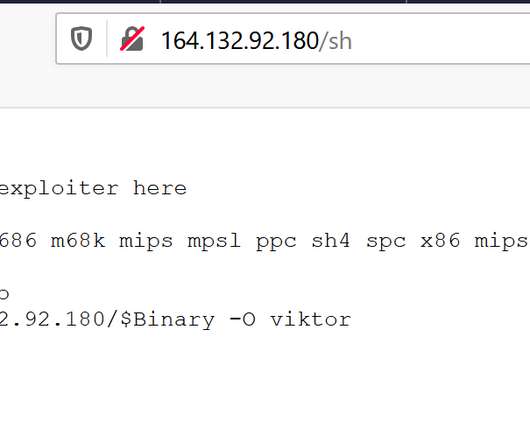
A newly discovered and previously undocumented UEFI (Unified Extensible Firmware Interface) bootkit has been used by attackers to backdoor Windows systems by hijacking the Windows Boot Manager since at least 2012. [.].























Let's personalize your content