Who’s Behind the Botnet-Based Service BHProxies?
Krebs on Security
FEBRUARY 24, 2023
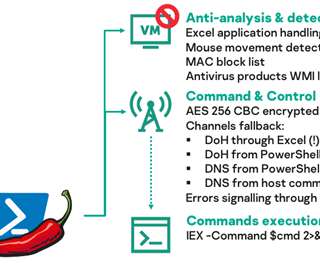
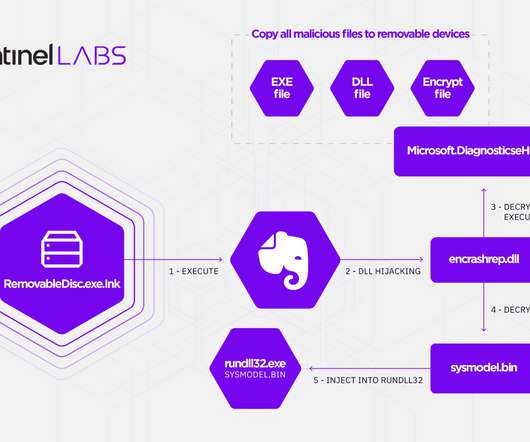
The Mylobot malware includes more than 1,000 hard-coded and encrypted domain names, any one of which can be registered and used as control networks for the infected hosts. BHProxies has authored 129 posts on Black Hat World since 2012, and their last post on the forum was in December 2022. The website BHProxies[.]com com on Mar.




























Let's personalize your content