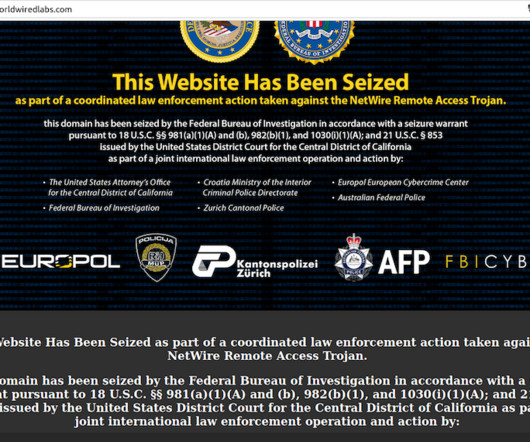
Law enforcement seized the website selling the NetWire RAT and arrested a Croatian man
Security Affairs
MARCH 10, 2023
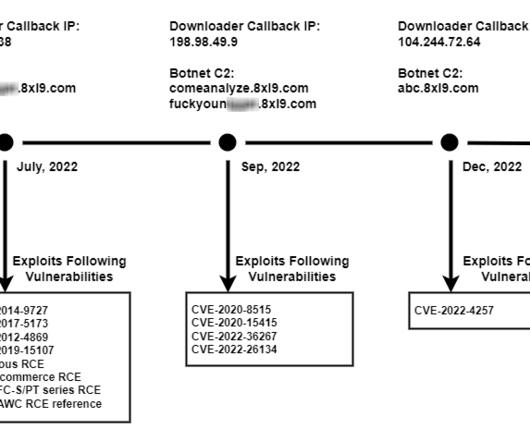
The NetWire Remote Access Trojan (RAT) is available for sale on cybercrime forums since 2012, it allows operators to steal sensitive data from the infected systems. DomainTools further shows this email address was used to register one other domain in 2012: wwlabshosting[.]com, ” reads the press release published DoJ.



















Let's personalize your content