New Mustang Panda campaign targets Asia with a backdoor dubbed DOPLUGS
Security Affairs
FEBRUARY 21, 2024
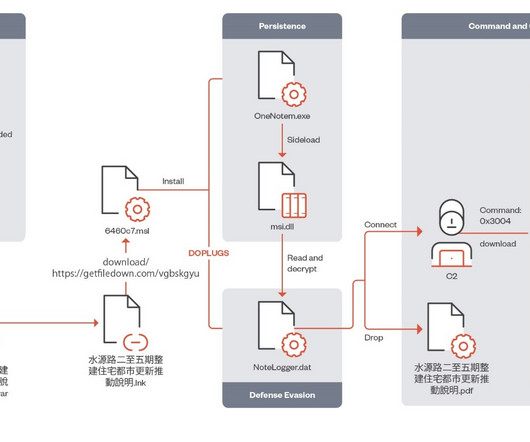
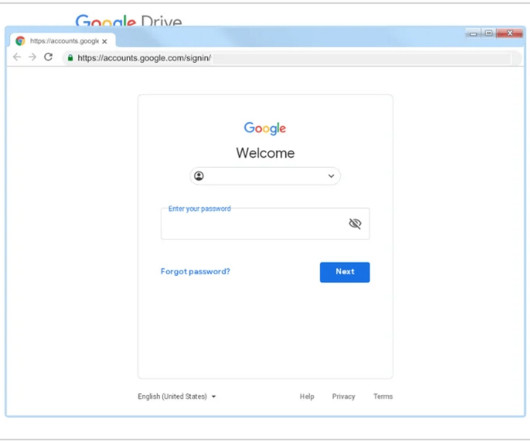
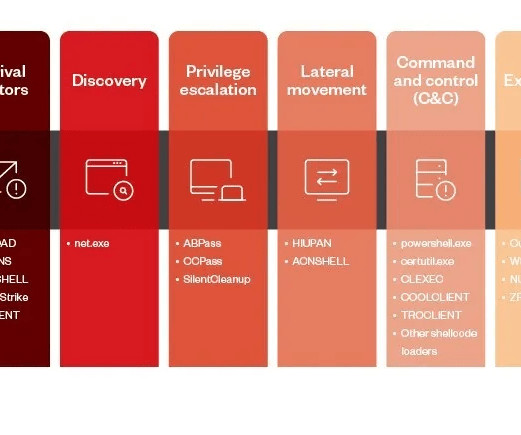
Mustang Panda has been active since at least 2012, it targeted American and European entities such as government organizations, think tanks, NGOs , and even Catholic organizations at the Vatican. “Based on our observations, we believe Earth Preta tends to use spear-phishing emails and Google Drive links in its attacks.”













Let's personalize your content