Law enforcement operation dismantled phishing-as-a-service platform LabHost
Security Affairs
APRIL 18, 2024
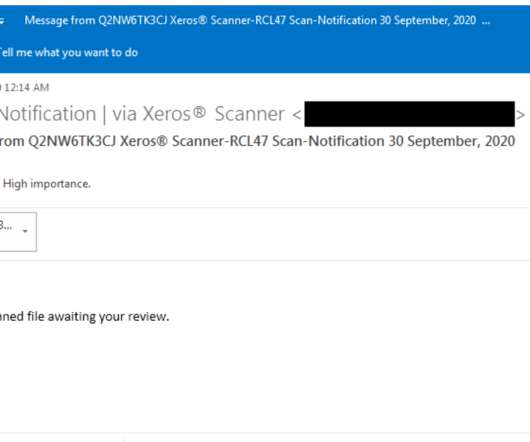
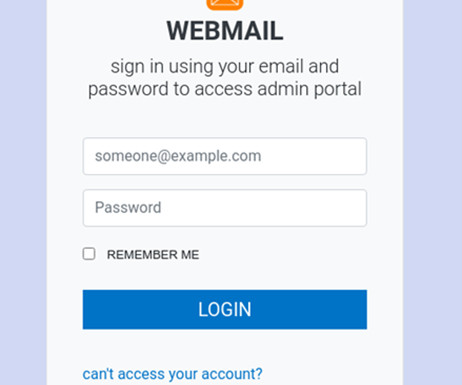
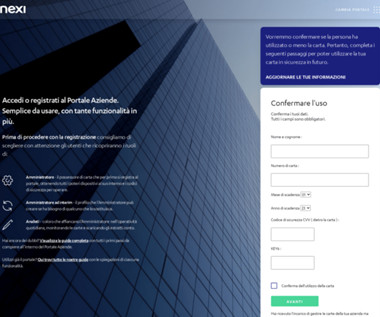
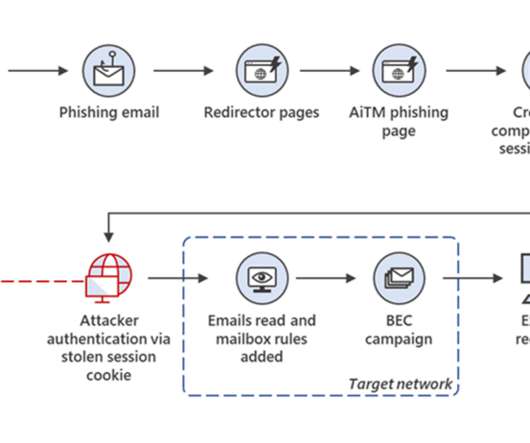
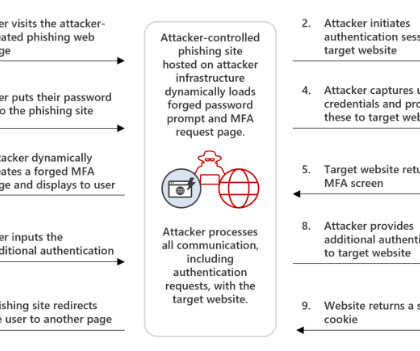
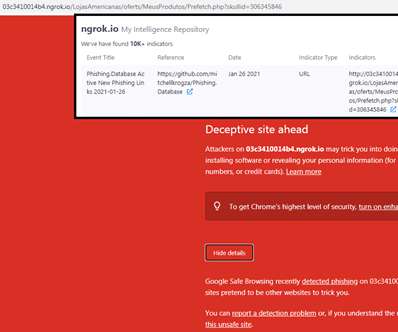
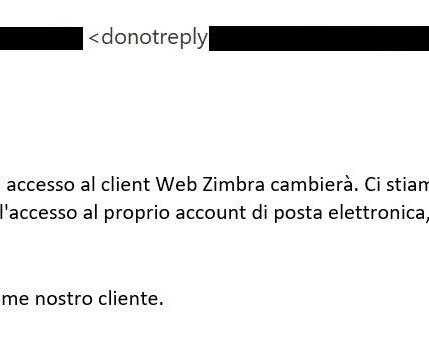
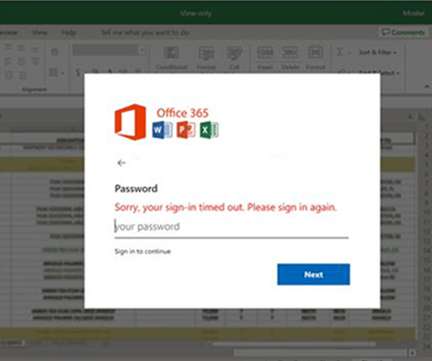
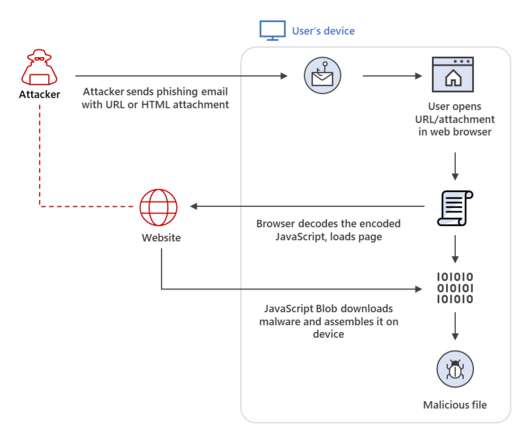
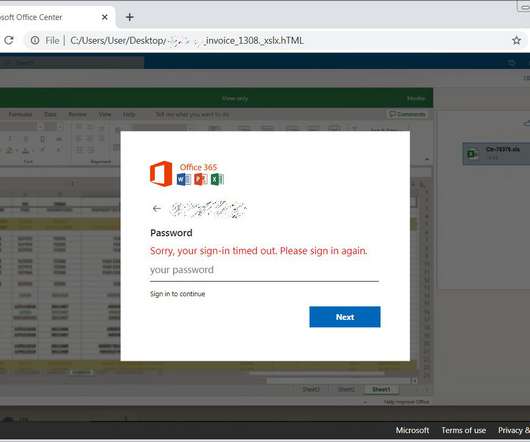
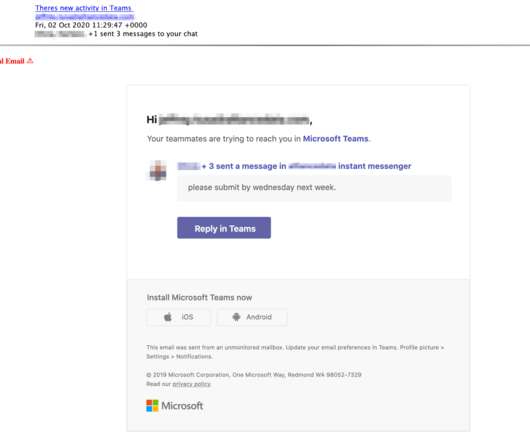
An international law enforcement operation led to the disruption of the prominent phishing-as-a-service platform LabHost. An international law enforcement operation, codenamed Nebulae and coordinated by Europol, led to the disruption of LabHost, which is one of the world’s largest phishing-as-a-service platforms.
























Let's personalize your content