The ticking time bomb of Microsoft Exchange Server 2013
DoublePulsar
DECEMBER 22, 2023
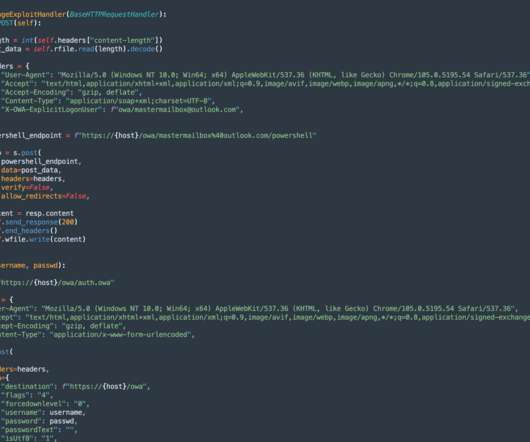
I’ve discovered two organisations with ransomware incidents, where the entry point appears to have been Exchange Server 2013 with Outlook Web Access enabled, where all available security updates were applied. But since there were a range of post authentication Exchange Server vulnerabilities this year ( link ), I doubt it is a zero day.







































Let's personalize your content