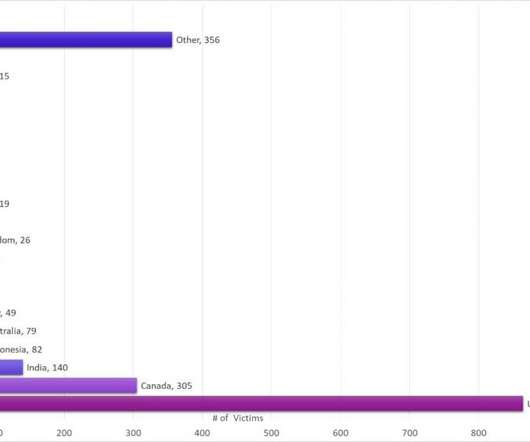
New ZLoader malware campaign hit more than 2000 victims across 111 countries
Security Affairs
JANUARY 10, 2022
A malware campaign spreads ZLoader malware by exploiting a Windows vulnerability that was fixed in 2013 but in 2014 Microsoft revised the fix. Experts from Check Point Research uncovered a new ZLoader malware campaign in early November 2021. banking Trojan and was used to spread Zeus-like banking trojan (i.e.

























Let's personalize your content