Financially motivated Earth Lusca threat actors targets organizations worldwide
Security Affairs
JANUARY 18, 2022
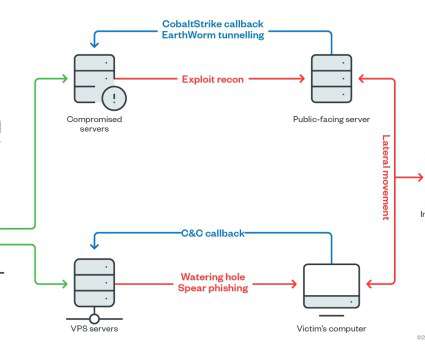
The Winnti group was first spotted by Kaspersky in 2013, but according to the researchers the gang has been active since 2007. This script shows a social engineering message, such as a Flash update popup or a DNS error, and attempts to trick the victim into downloading a malicious file deploy a Cobalt Strike loader.














Let's personalize your content