Arrest, Raids Tied to ‘U-Admin’ Phishing Kit
Krebs on Security
FEBRUARY 8, 2021
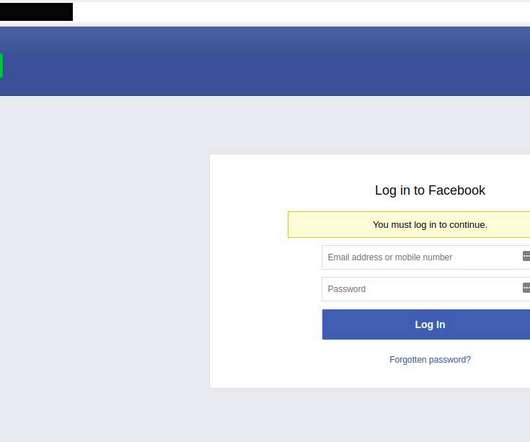
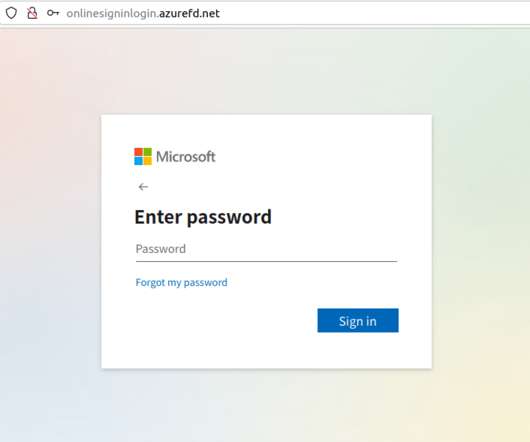
Cyber cops in Ukraine carried out an arrest and several raids last week in connection with the author of a U-Admin , a software package used to administer what’s being called “one of the world’s largest phishing services.” The U-Admin phishing panel interface. Image: fr3d.hk/blog. ” U-Admin, a.k.a.










































Let's personalize your content