Bomb Threat, Sextortion Spammers Abused Weakness at GoDaddy.com
Krebs on Security
JANUARY 22, 2019
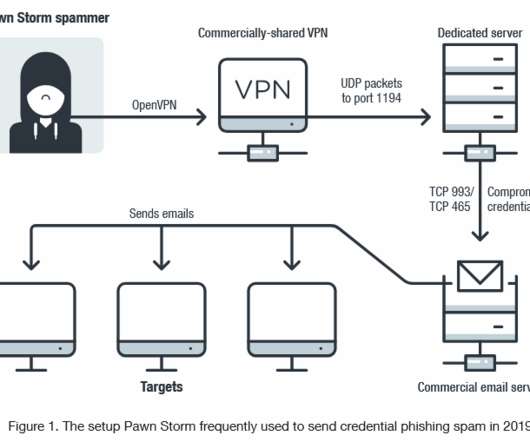
Experts at Cisco Talos and other security firms quickly drew parallels between the two mass spam campaigns, pointing to a significant overlap in Russia-based Internet addresses used to send the junk emails. Large-scale spam campaigns often are conducted using newly-registered or hacked email addresses, and/or throwaway domains.

































Let's personalize your content