Russian-speaking cybercrime evolution: What changed from 2016 to 2021
SecureList
OCTOBER 20, 2021
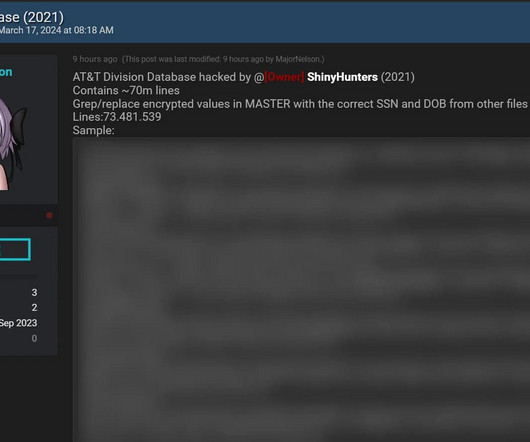
Back in 2016, the primary focus of our expert was on major cybergangs that targeted financial institutions, banks in particular. Many used browsers that they were accustomed to, not browsers of choice, or default browsers set by organizations, such as the Internet Explorer. The year 2016 saw banks in Russia hacked one after another.












































Let's personalize your content